
Introduction
Blockchain’s transparency, while promoting trust, presents challenges for data that require privacy. This is especially crucial in trustless gaming, where multiplayer games risk exposing sensitive data, leading to issues like cheating and system manipulation. While zero-knowledge proofs (ZKPs) games such as Snarky Monsters are currently being explored, they only generate proofs for each completed game, with all else remaining off-chain.
Fhenix introduces Fully Homomorphic Encryption (FHE) to address this, whereby proofs are produced for individual game moves. FHE as a whole allows developers to integrate confidential computing into workflows using familiar EVM languages like Solidity. With FHE, data can be encrypted for privacy while still updating the network’s shared state transaction-by-transaction, enhancing data security and trust in trustless gaming.
This article explores FHE’s implementation in the trustless gaming sector, specifically for PVP games:
An overview of trustless gaming.
ZKP limitations.
FHE’s ability to incorporate privacy and security.
Utilizing FHE Rollups as low-level gaming infrastructure.
Worth noting is that our confidential computing technology is not a replacement to games, but rather infrastructure to support higher levels of the gaming stack. FHE’s encryption capabilities can be easily implemented into any workflow and holds the key to enhancing decentralization, security, and privacy for all users—a vital component for Web3’s successful adoption at scale.
On-Chain Gaming
Trustless gaming is an umbrella term that refers to the various gaming environments taking place on the blockchain, such as player-vs-player games, casino games (poker, blackjack, etc), prediction markets, e-sports, AR/VR-related games, and more. The trustless aspect refers to the fundamental blockchain design principle of eliminating trust between participants, in stark contrast to traditional gaming or gambling platforms that require the trust of a central authority or intermediary.
This sector holds immense potential, especially when considering that Web2 gaming has 2.7 billion annual users and is projected to generate $490 billion in revenue by 2023. And these figures exclude other sectors, such as the $87 billion online gambling market and the rapidly emerging AR/VR sector. However, the public nature of blockchain is currently ill-suited for trustless gaming from both a privacy and security perspective.
Let’s consider on-chain casino gaming.
Various limitations make them ill-suited for the blockchain at present:
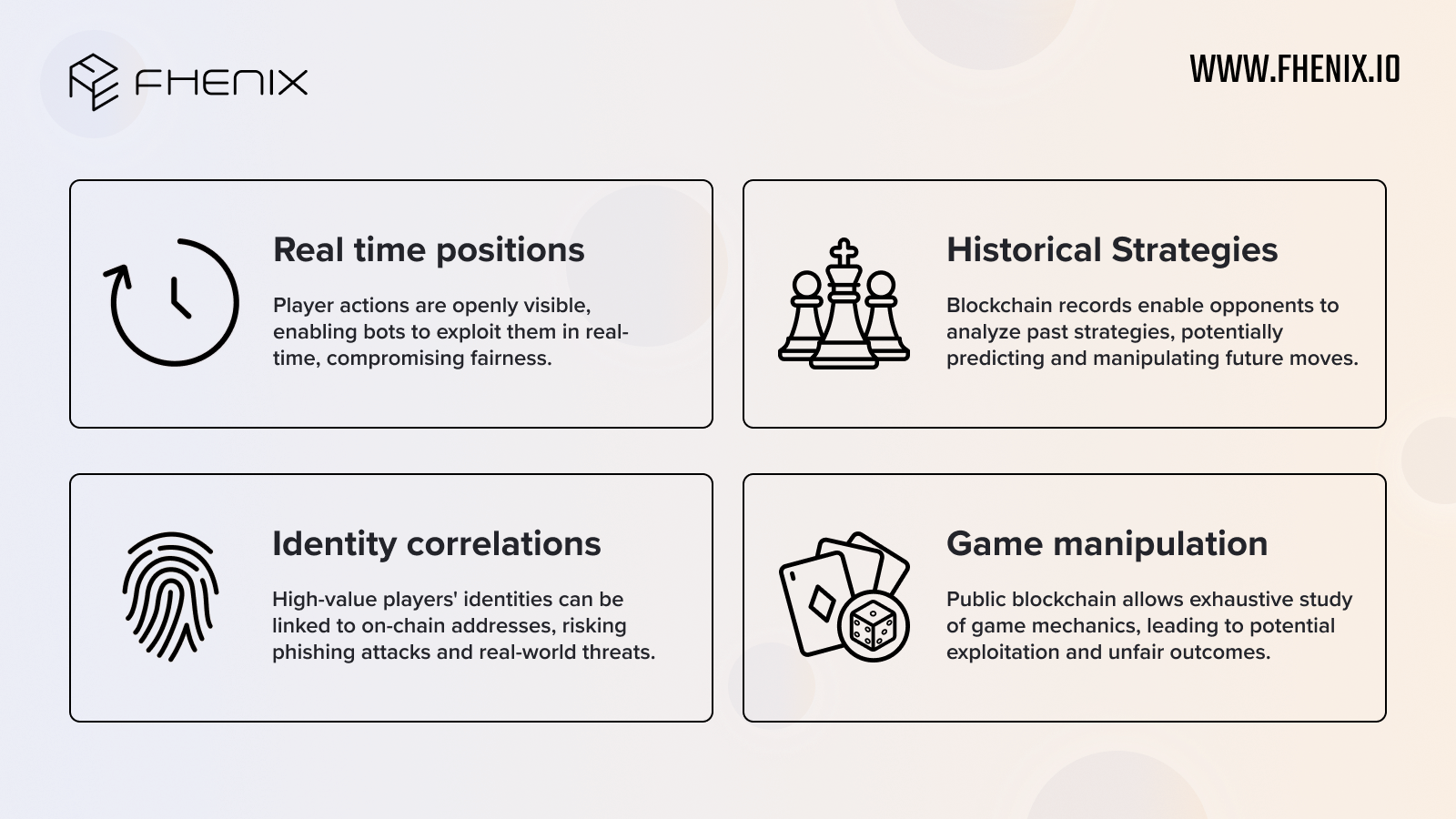
Real-Time Positions: Player actions are openly visible, enabling bots to exploit them in real-time, compromising fairness.
Historical Strategies: Blockchain records enable opponents to analyze past strategies, potentially predicting and manipulating future moves.
Identity Correlation: High-value players’ identities can be linked to on-chain addresses, risking phishing attacks and real-world threats.
Game Manipulation: Public blockchain allows exhaustive study of game mechanics, leading to potential exploitation and unfair outcomes.
Existing Approaches
A common existing approach used by projects such as Dark Forest and zkHoldEm is to rely upon zero-knowledge proofs (ZKPs) to bring privacy to gaming. ZKPs are great for compression as they can bundle many transactions into a single update, making them quite scalable while maintaining data privacy. This is useful in gaming, and zkHoldEm is one such example that works by having their zkShuffle smart contract provide encryption for each poker hand. Before each hand, players each shuffle the deck once and encrypt the result. When their hand is dealt, they decrypt their cards for all of the players to see. This, and details for other aspects of each poker hand, are verified through ZKPs.
However, this approach requires the game state to be updated on-demand each hand, with players each shuffling the deck and passing it on. We’d also argue that this approach is not very transparent. As mentioned with Snarky Monsters, ZKPs tend to be used for each game, rather than for each action. Even if a game claims to be fully honest and use ZKPs, it can be hard to verify this and reliance is placed on their off-chain integrity and systems. In the context of a Player-vs-Player (PvP) game like rock-paper-scissors, imagine a player losing 8 times in a row. It would be hard to prove the randomization occurred honestly, and the player may refuse to continue playing.
It’s also more complex this way – consider again the rock-paper-scissors game. On the blockchain (without FHE) a commit-reveal scheme is likely to be used, whereby a player’s choice is cryptographically committed, creating a “sealed envelope” of sorts. After all players have committed their choices, they reveal their actual choices, and the game’s outcome is declared. This provides a poor interface as multiple rounds of interaction are required which increases complexity.
FHE enables an improved approach with built-in transparency as each in-game move is on-chain and updates the blockchain’s state, verifiable via decryption. Async updates, rather than requiring players to shuffle cards each hand, are also possible as the card decks can be set up async.
With rock-paper-scissors where responses are encrypted on the blockchain using FHE, blockchain state updates can be made in real-time. The data is then decryptable once privacy is no longer required. This eliminates reliance on a single ZKP, as all data and computations can be verified.
This is possible with FHE technology.
FHE on the Blockchain
FHE is a game-changer for blockchain-based gaming. It ensures data remains encrypted from start to finish, enhancing decentralization and safety. User actions are encrypted on the blockchain, computed upon with FHE, and then decrypted to provide transparency and trust. It is fully on-chain with the blockchain’s state synchronously updated for all, ensuring privacy and security, and enabling new blockchain use cases.
It’s important to note that we are not competing with games themselves, as we wish to see them succeed and advance the industry together. Rather, we are a low-level infrastructure for confidential and secure computing that supports higher levels of the gaming stack. For example, FHE can be a base from which gaming ecosystems develop with privacy and security built-in through incorporating FHE technology at their core.
One promising avenue for achieving this is through Fhenix’s FHE Rollups, which empower developers to create custom app chains with FHE seamlessly integrated, all while using familiar Ethereum Virtual Machine (EVM) languages. For instance, one FHE rollup could be dedicated entirely to casino games, ensuring the complete privacy and security of these games. Meanwhile, another rollup, fully interoperable with the first, could focus on large-scale player-versus-player (PvP) games.
Is this already possible?
Yes, but given FHE’s complexity, there is a latency period that makes FHE best for games where actions are not time-sensitive, such as strategy games or casino games. This is to be expected of a nascent, cutting-edge technology, but we expect speed to rapidly improve throughout 2024 and into 2025, as FHE adoption increases as well.
Conclusion
Blockchain-based gaming, often referred to as trustless gaming, faces privacy and security challenges due to blockchain’s inherent transparency. While Zero-Knowledge Proofs (ZKPs) are a solution, they may not be ideal for gaming since they hide all actions behind a single ZKP. Fhenix’s FHE technology, on the other hand, allows encrypted data to synchronously update the blockchain’s state and be decrypted as needed, offering privacy, security, transparency, and trust.
Developers can easily integrate FHE into their workflow using familiar Ethereum Virtual Machine (EVM) languages, promoting fairness and equality in blockchain-based gaming. While FHE may not be as scalable as ZKPs currently, it’s advancing rapidly, making now an opportune time for developers to get involved.
Fhenix’s mission is to usher in a new era of computing, prioritizing privacy and security, and ultimately eliminating data breaches while maintaining confidentiality and data integrity for all.
We also recommend visiting our website at fhenix.io to learn more.


